
The Call Centre Security Experience Scorecard benchmarks your organisation’s ability to effectively and efficiently welcome callers to your contact centres. To make this assessment and provide you with recommendations for improvement, we need to know some key facts about your organisation and how the process currently performs.
Are you ready?
You may be able to jump straight into the scorecard and get started. The questions are self-explanatory, and you probably have the majority of metrics to hand or can make educated guesses, but if you want to make sure you have all the required information, we’ve prepared this short guide to guide you.
You will need a good grasp of how the process performs today, but we’re generally only looking at +/- 5% in terms of accuracy, so it may be easier just to get started and come back here if you get stuck.
Table of Contents
About You
Before you start, we need to know your name, email address and phone numbers to send you your results. As soon as you’ve done this, we’ll send you an email with a unique link that enables you to come back to your scorecard at any time.
You need to agree to us processing your information, but you don’t have to sign up for our newsletter if you don’t want, although you’ll definitely miss out if you don’t.
Automation
So we only ask you relevant questions; we ask you to confirm whether you use automated systems for caller identification, authentication, routing or self-service before your calls connect with agents.
Saving Progress – From this step onwards, we will save your entries locally in your browser (using cookies), so you can return at any time, but it’s best to try and complete it in one sitting.
Identification and Authentication
Over time many organisations have conflated these two distinct processes into a single process known as security, verification, identification and verification, ID&V or similar. To get the most out of the scorecard, we need to understand how these process steps perform independently as they both have quite different impacts on usability, efficiency and security. For clarity, we define them as follows:
- Identification – the process of identifying the unique record in your systems that the caller is claiming to represent.
- Authentication – The process of testing a callers claim of who they are to provide information and/or service.
For manual and automated (if you use them) approaches, we will ask you for up to the three most frequently used forms of identification and authentication as well as the percentage of callers using each of them and when they are completed manually, how long it takes your agents to complete them.
Identification Methods
There are so many ways of identifying callers in your system of record we couldn’t possibly show them all, so instead, we’ll ask you to categorise your method into one of 5 categories:
- Organisation Based Identifier – This is usually something you have issued to the caller, such as an account number, username or reference number.
- Government Issued Identifier – This is usually something issued by an organisation other than yourselves (most often the Government) and includes items like Social Security and National Identification numbers but could include phone numbers.
- Personal Identifier – These are usually more personal to the caller, either their name or some other personally generated item like a username they can choose themselves.
- Geographic Identifier – This is usually part or all of the caller’s correspondence, billing or service address.
- Calling Line Identifier (CLI) – Also known as Automatic Number Identification (ANI), this is the identification provided to you by the telephone network with no engagement required from the caller. If you actually ask for their phone number, this is most like a government-issued identifier.
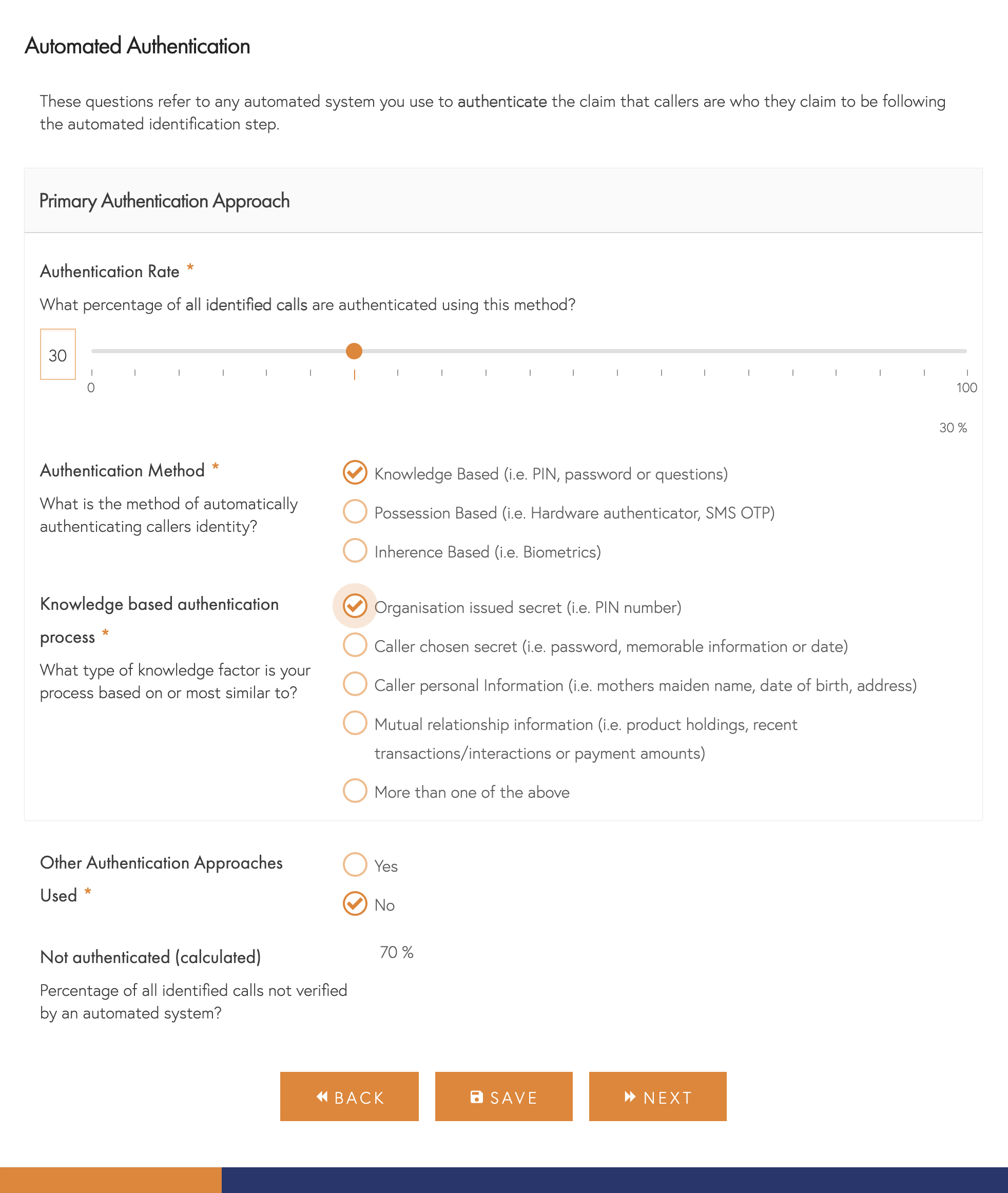
Authentication Methods
Similarly to identification methods there are far too many different permutations and combinations to include so we have categorised them into 3 major types with a few subcategories for each as follows:
- Knowledge-Based – This method is dependent on the caller knowing some information and your automated system or agent challenging them for it. This is by far the most common method of authentication today and has several subcategories:
- Organisation Issued Secret – This is usually a PIN or similar issued by yourselves and which you protect in transmission and in your systems to minimise exposure.
- Caller chosen secret – This is usually an item or items chosen by the caller, although it may be from a list of types you ask them for. Most often, this takes the form of a password or number but can also include memorable dates and places or even favourite colours and childhood friends. It is different from the next category in that it doesn’t have to be based on fact.
- Caller personal information – The most common form of knowledge-based authentication is often items like the caller’s mothers maiden name or date of birth based on verifiable facts. It could also include current or previous address, where they went to school/college or similar.
- Mutual Relationship Information – This covers items that are likely only known to your organisation and the caller, such as the products they hold with you, recent transactions or how they pay their bills.
- More than one of the above – Your authentication process may rely on more than one of the above, in which case select this item or the item that you consider most central to your process
- Possession Based – This method depends on the caller having an item in their possession and challenging them to prove they have it. Often this involves a time-based challenge. There are 4 main categories:
- Phone-based – This is based on them having access to a phone, either mobile or landline, to which you send an SMS or Text Message with a unique code. It could also include approaches that call back on a known or registered number either with or without a code.
- Hardware-Based One Time Passcode – Most commonly seen in enterprise remote access, this will often be a key fob or mini calculator like device that requires the user to read out the displayed number that changes regularly. It doesn’t include approaches where a separate card is inserted into the device but may include devices that require a pin or challenge code to be entered.
- EMV Chip and PIN – This requires the user to place the debit, credit or similar smart card in a device and use their PIN to get a one-time passcode or a response code to a challenge.
- Software/app-based – This approach uses an app installed on a smartphone or other device to generate a one-time passcode that changes regularly. It may use standards-based approaches such as google authenticator or be embedded inside your own app. It may also include mechanisms that use your own app features to secure inbound phone calls or two way messaging requiring the user to log in to the app on their device to verify they are making the call.
- Inherence Based – The final category is based on the caller’s physical and behavioural attributes and is often also known as Biometrics. In the telephony channel, only Voice Biometric is really applicable, and there are two principal approaches:
- Text-Dependent – The caller is registered saying a specific phrase, phrases or digits and then verified by repeating them when they complete identification on subsequent calls. This approach is most commonly used in automated systems.
- Text Independent – This method relies on comparing previous recordings of the caller as they speak to an agent during a normal conversation and is usually used when speaking to an agent.
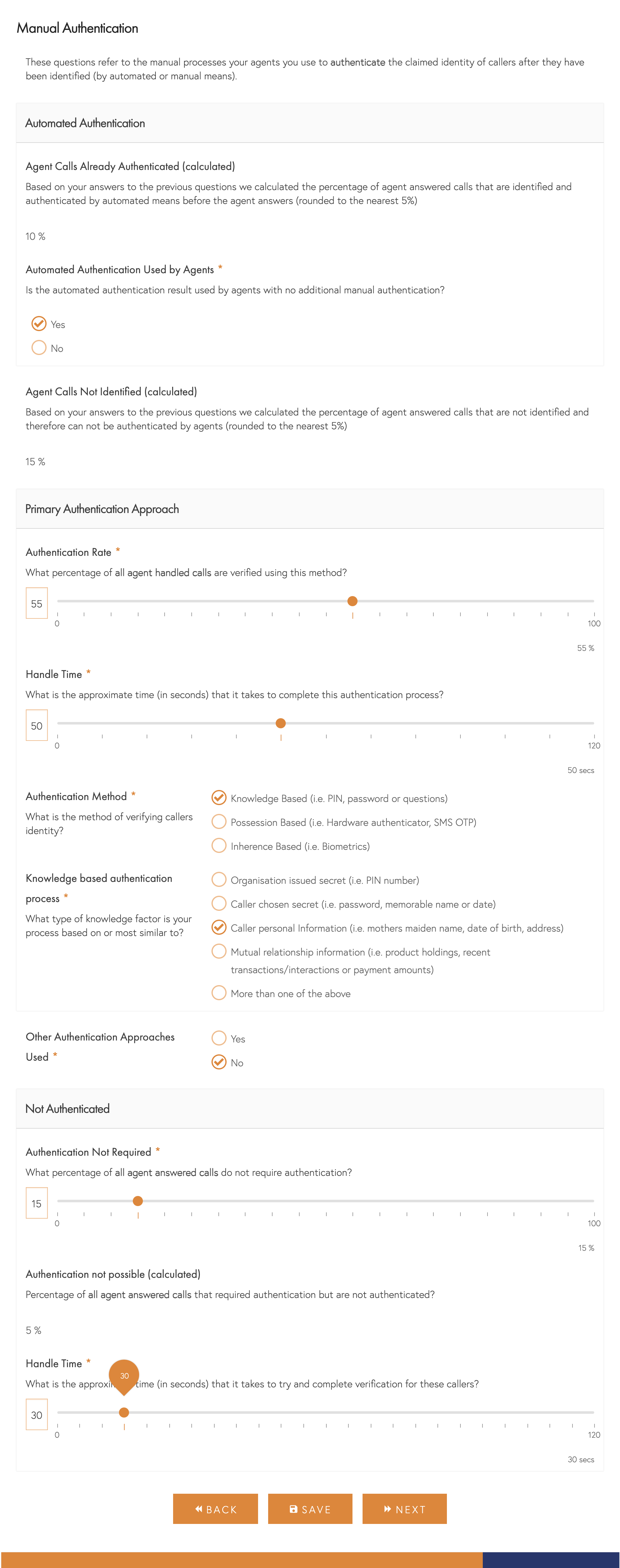
Handle Time
For manual identification and authentication, we will ask for the approximate handle time of each method. If you haven’t had the opportunity recently, it’s well worth sitting side by side with agents and observing the process whilst also taking rough note of the time each approach takes. We are really looking for how long each process takes on average, so exclude any time spent on pleasantries when measuring. You don’t need to be particularly accurate here (to the nearest 5 seconds is perfect), and if you don’t have the opportunity to observe, then use your best guess based on your own experience.
Rates
One of our key tools for understanding and communicating Call Centre Security Experience performance is our Security Path Visualisation (you’ll get a personalised version in your detailed report), but this does require a reasonably detailed understanding of how callers flow through the different process steps.

We’ve tried to make it as easy as possible by asking for numbers that are likely to already exist in your organisation and have a different approach for automated and manual approaches.
- Automated System – We find most organisations think of this as a conversion process. For identification, authentication and self-service, we will ask you for the percentage of callers that use each method as a percentage of all those who start it. As a check, we will calculate and show you the percentage who didn’t complete it based on your answers.
Screenshot – Identification and Authentication - Agents – We find most organisations refer to the total number of calls handled by agents. Hence, we ask for the proportion of total agent-handed calls that each method or approach applies to. We’ve made it easier for you by calculating what proportion you don’t need to account for with each step (because they can’t be identified or have already been verified by an automated system, for example). We’ll also ask what percentage of calls handled don’t need to complete the process to meet their needs. As a check, we will calculate and show you the percentage who didn’t complete it based on your answers. If that percentage is less than 0, we’ll display a warning as one of your entries either on that page or earlier may be off.
As with handle time, the more accurate you can be, the better, but to the nearest 5% is generally close enough. We round all our calculations to the nearest 5% anyway.
Routing
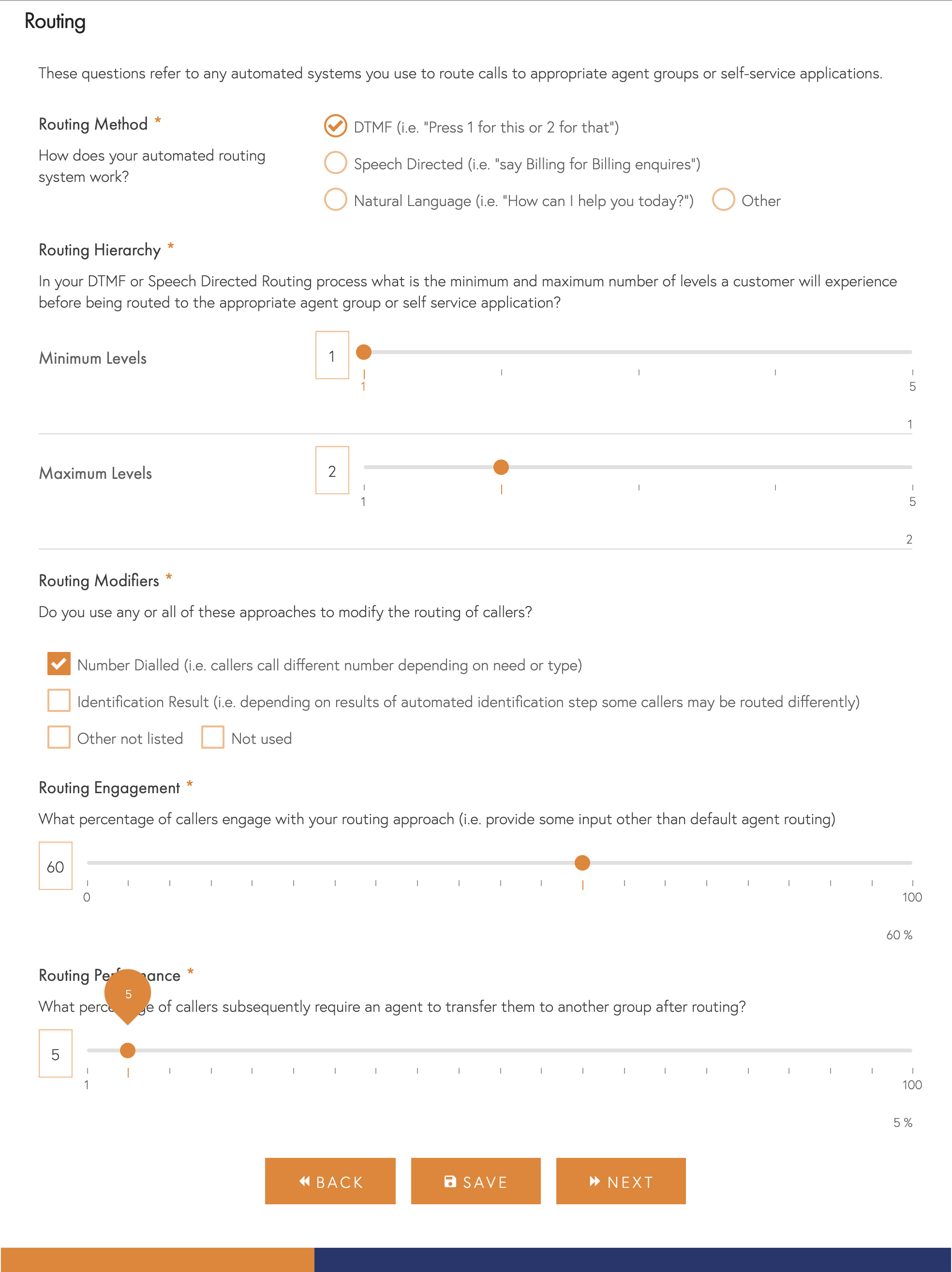
We will only ask these questions if you confirmed that you used automated methods to route callers.
- Method – The approach you use to capture callers intent, such as using a key-based menu, directed speech or natural language understanding.
- Routing Hierarchy – If you use a keypad-based or speech-oriented menu, what is the minimum and the maximum number of levels a caller might experience. i.e. can they get routed after just 1 selection in some cases, and for the most complex, how many levels might they have to navigate.
- Modifiers – Do all callers experience the same routing approach, or do you modify the approach based on the number they dialled, who they have been identified as or other methods.
- Engagement – Some callers will not provide any input, but the majority will. How many callers provide a meaningful input that you use for routing (other than a default agent request).
- Performance – We measure performance based on the number of times a caller has to be transferred to another agent group or team following routing.
Self-Service
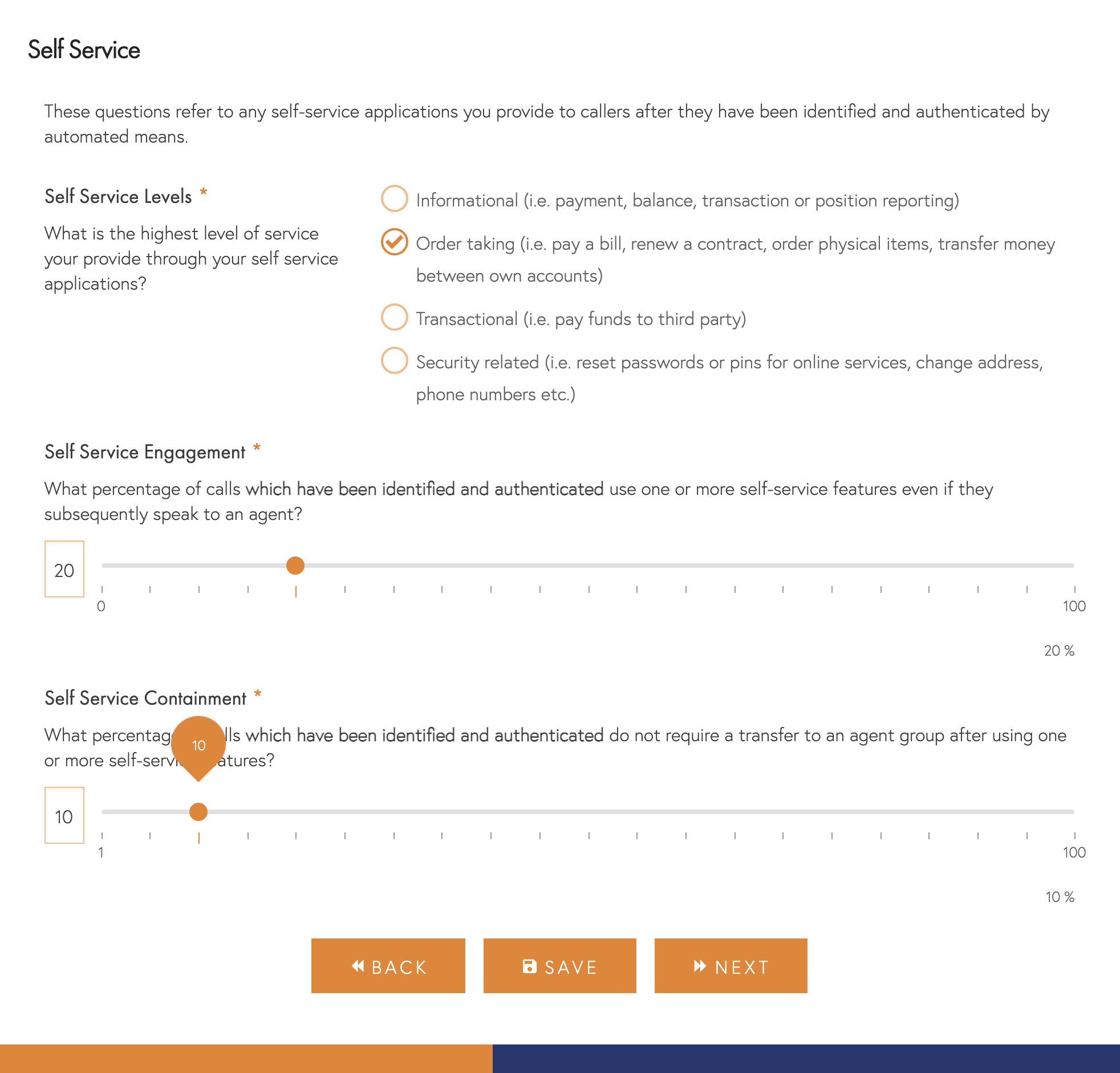
We will only ask these questions if you confirmed that you provided self-service capabilities to callers.
- Levels – The highest level of service available to callers, with informational requests being the lowest and security-related requests being the highest. Of course, the nature of these services will vary according to your industry, so please select the nearest match for your particular organisation.
- Engagement – Some callers will not engage with self-service features or be unable to complete the step. Please indicate what percentage of callers who are identified and authenticated complete one or more self-service steps. If your system plays balance or similar information to all callers regardless of their request, please ignore them and only include callers who engage with more sophisticated features.
- Containment – Some callers will have all of their needs met by your self-service capabilities, but others will still need agent assistance. Please indicate how many callers hang up after using one or more self-service features.
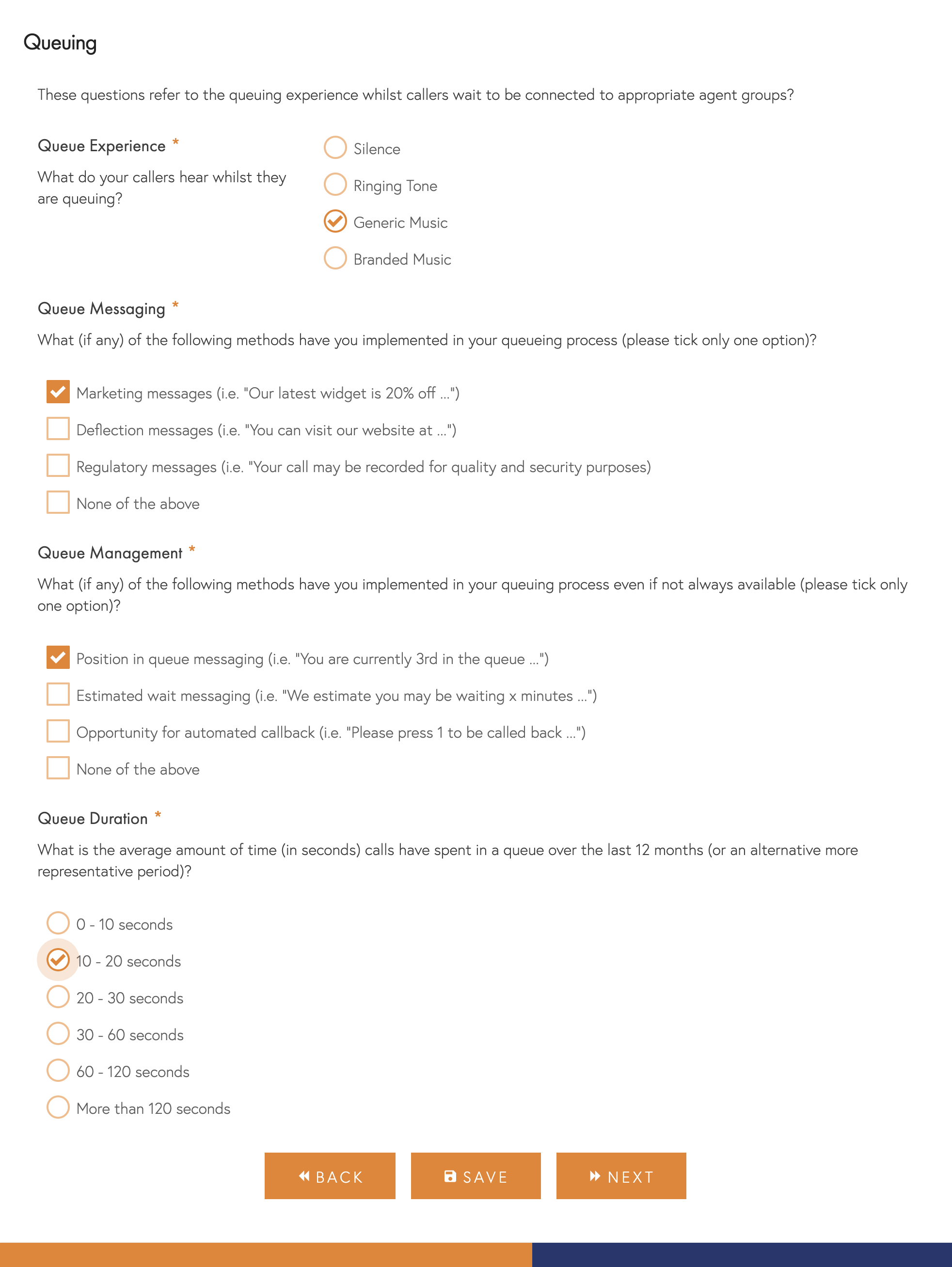
Queuing
We will ask these questions to all respondents to understand the caller queuing experience.
- Experience – When callers are queuing, what do they generally hear.
- Messaging – When callers are queuing, do you play them any additional marketing messages. Please include any regulatory messages related to recordings.
- Management – How do you manage callers expectations of their wait time. There are a variety of approaches, including automated callback and place in queue holding.
- Wait Times – On average, over the last 12 months, what has been your caller wait time.
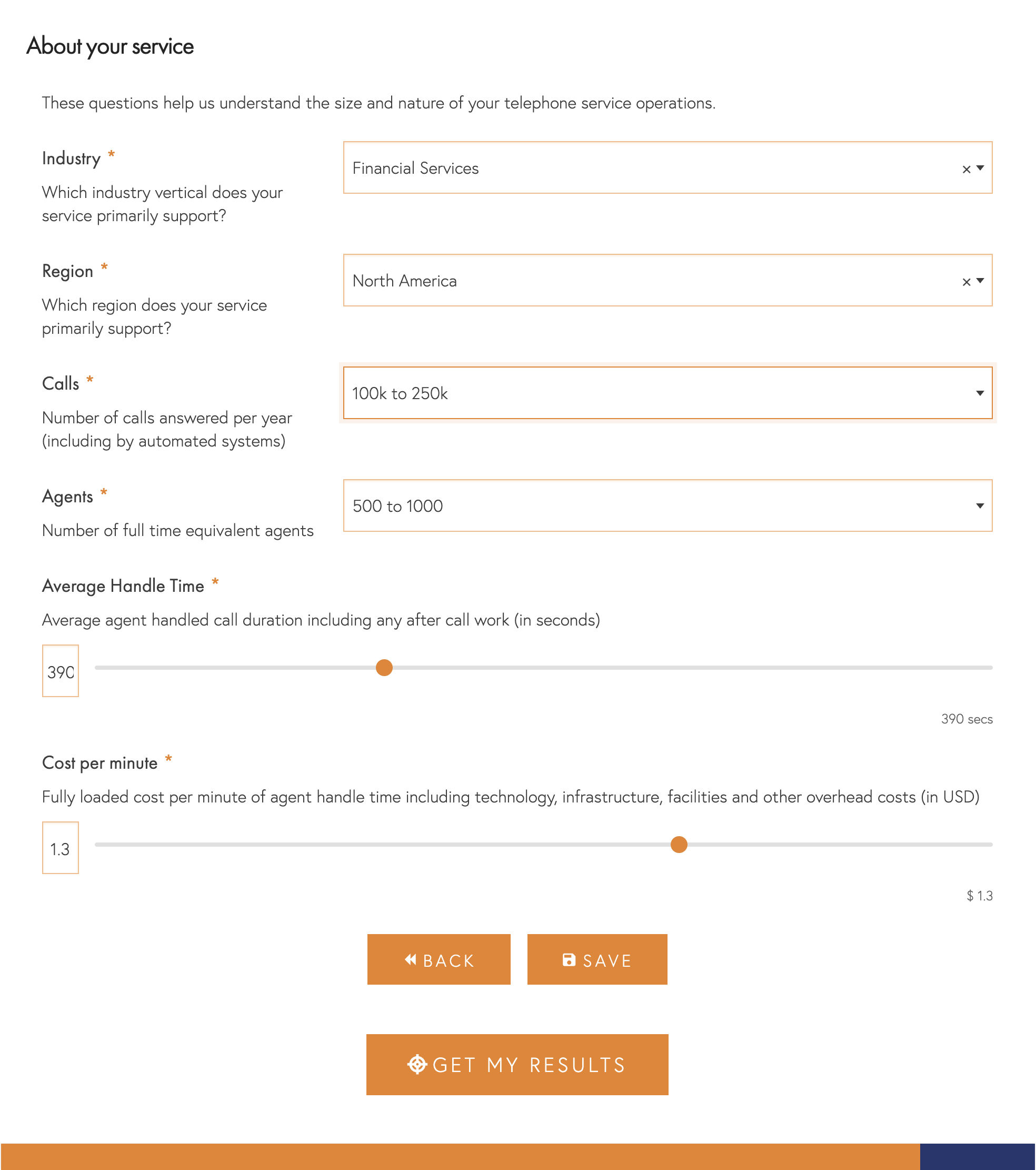
Your Organisation
To put your answers in context and provide more specific recommendations, it’s important to understand your organisation’s nature, its scale, location, and the industry in which it operates.
When calculating the cost per minute of agent handle time, please include your organisation’s wider infrastructure costs. This helps us to size the value of any recommendations we might make, but if you don’t have this information, then please enter your directly controlled costs (i.e. salary, pension, training, the proportion of team leader etc.)
Get Your Results
When you click “Get Your Results” you will be redirected to our results page with a very high-level score for the Usability, Efficiency and Security of your security process. We’ll also send you an email with these scores. You can read more about how we calculate these scores here.
As soon as I have fully processed and reviewed your data I will be in touch with your detailed assessment and recommendations. If you need to change any of the information you have entered in the interim then please contact me at hello@symnexconsulting.com.
How does your Call Centre Security process really perform?
Popular Posts


