It's not often that your world gets "Altmaned". My feed lit up early yesterday morning with what appeared to be offhand remarks made by Sam Altman, CEO of OpenAI, during an interview at the Federal Reserve's Large Banks Conference.
In response to a question about using AI to mitigate fraud risks from impersonation, he was categorical: "I am terrified that some financial institution will accept a voice print as authenticationAuthentication is the call centre security process step in which a user's identity is confirmed. We check they are who they claim to be. It requires the use of one or more authentication factors. to move a lot of money." He went on to claim that AI had "fully defeated" most authentication methods beyond passwords.
My reaction? He's not wrong... but he's not right either.
What Altman Gets Right
The threat is real. I first added synthetic speech to my risk tracker in 2009 and have watched the technology accelerate ever since. Today's synthetic speech and voice cloning capabilities are genuinely impressive, indistinguishable to the human ear. With my automation hat on, this enables magical customer experiences. With my securitySecurity is one of three key measures of Call Centre Security process performance. It is usually expressed as the likelihood that the process allows someone who isn't who they claim to be to access the service (False Accept). hat on, it's concerning.
The specific threat Altman references, using voice cloning to defeat voice biometric authenticationAuthentication is the call centre security process step in which a user's identity is confirmed. We check they are who they claim to be. It requires the use of one or more authentication factors., sits at the pinnacle of my synthetic speech threat hierarchy. In real-world tests the latest voice cloning capabilities have a better than even chance of fooling voice biometricsVoice Biometrics uses the unique properties of a speakers voice to confirm their identity (authentication) or identify them from a group of known speakers (identification). authentication. There are still technical limitations around how much audio is needed and speed of generation, but these will be overcome.
No one close to these technologies is surprised. The question isn't whether this attack is possible, it's what we do about it.
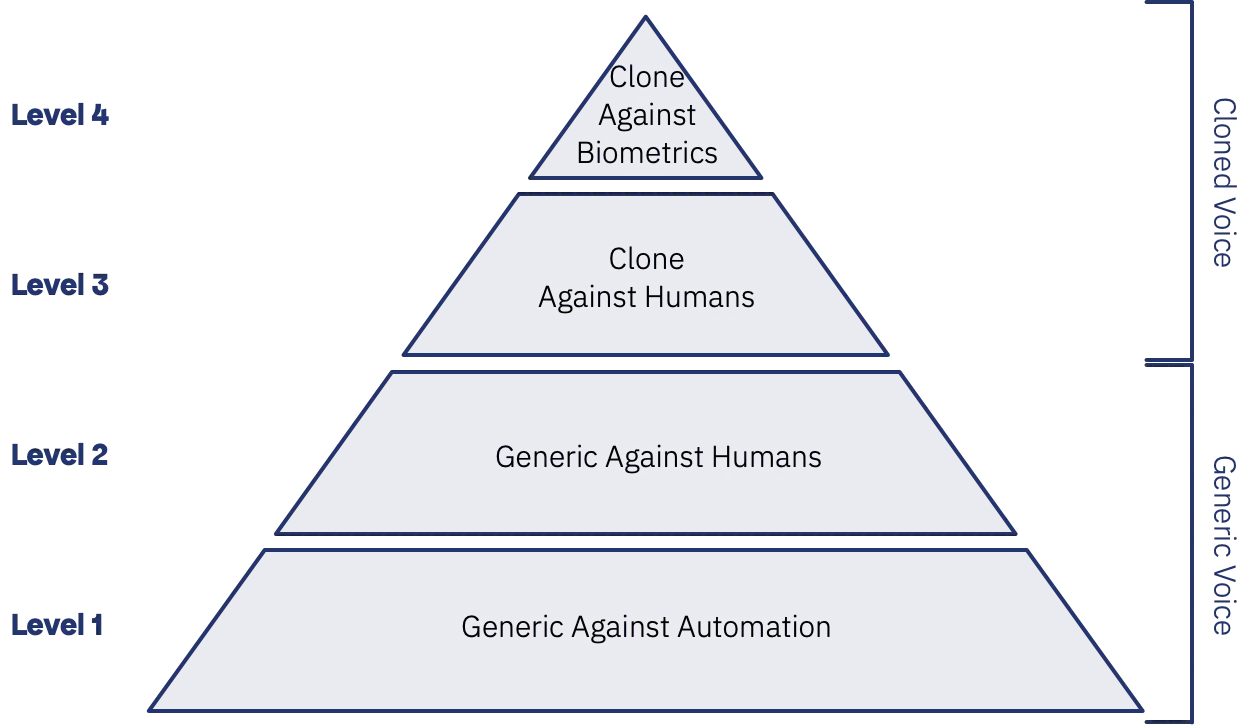
The Call Centre Reality Check
Here's where Sam's Silicon Valley perspective collides with reality: The voice channel is the lowest common denominator for customer service. Everyone has access to a phone, even if it's just a communal landline. They use their voice to communicate information, intent and instructions. After 150 years, that's about the only thing organisations can take for granted.
The organisations I work with collectively handle hundreds of millions of calls every year and know that perfect securitySecurity is one of three key measures of Call Centre Security process performance. It is usually expressed as the likelihood that the process allows someone who isn't who they claim to be to access the service (False Accept). is an impossible pipe dream. They have to walk a careful tightrope of an ever changing threat landscape against their customers’ needs to access their services in an efficient way. Today, more customers are locked out of their accounts by forgotten PINs and passwords than are compromised by fraudsters, deepfake or otherwise.
Security perfectionists will point to more secure authenticationAuthentication is the call centre security process step in which a user's identity is confirmed. We check they are who they claim to be. It requires the use of one or more authentication factors. approaches. Altman himself sells iris scanners through Worldcoin. However, organisations must select approaches that are usable by the average person, when they need them, at an appropriate price point for the risks they're mitigating.
Perfect security that no one can use isn't security, it's abandoned calls and frustrated customers.
Subscribe for New Content
Defence in Depth
All this means that modern call centre securitySecurity is one of three key measures of Call Centre Security process performance. It is usually expressed as the likelihood that the process allows someone who isn't who they claim to be to access the service (False Accept). can't rely on any single authenticationAuthentication is the call centre security process step in which a user's identity is confirmed. We check they are who they claim to be. It requires the use of one or more authentication factors. factor. Even if they have deployed voice biometricsVoice Biometrics uses the unique properties of a speakers voice to confirm their identity (authentication) or identify them from a group of known speakers (identification)., not every customer will be registered, so there will always be a mix. The factors used and their combination invariably depends on both availability and the risk associated with the thing they are trying to do.
When calls start organisations need to be reasonably sure who the caller is and that they are who they claim to be but the priority is understanding their request. As calls progress, more information emerges about the caller's intent and transaction risk. Additional factors can be triggered if more authentication strength is needed for the request, or before giving out critical information. Detection capabilities run in the background, identifying anomalies in behaviour and requests. Finally, as calls wrap up and requests are finalised, all these data points combine to inform whether to act on the caller's instruction.
Voice biometrics is never implemented in isolation (even if it sometimes appears that way to an outsider), organisations build layered defences that balance security, usabilityUsability is the primary performance dimension of the security process. Get it right and both security and efficiency flow, but usability is all wrapped up in human psychology. It’s a complicated subject deeply linked to behaviour, not just that of customers, but also of call-centre agents. and efficiencyEfficiency is one of three measures of Call Centre Security process performance. It represents the actual and opportunity cost of the security process, for example the costs of agent time spent on manual authentication or the missed opportunity for self-service.. This messy reality of serving diverse customers with varying capabilities shapes every implementation decision. It's not elegant but it works.
Related Services
Detection: The Missing Half of the Story
Altman's warning misses a critical capability: we detect as well as authenticate. Voice clones inherently leave detectable signatures. Voice biometric systems should check both that "you are who you claim to be?" and "you are a real person?"
Unfortunately this, detection capability, is not a set-and-forget solution but an ongoing process requiring active management and vendor partnership. The cat-and-mouse game between synthesis and detection is another messy reality that theoretical discussions ignore.
Detection doesn't guarantee perfect securitySecurity is one of three key measures of Call Centre Security process performance. It is usually expressed as the likelihood that the process allows someone who isn't who they claim to be to access the service (False Accept). either but it shifts fraudster economics, making attacks more expensive and less scalable.
The Other Layers Altman Misses
Voice biometricsVoice Biometrics uses the unique properties of a speakers voice to confirm their identity (authentication) or identify them from a group of known speakers (identification). rarely operates alone and as the threat evolves organisations will add more capabilities to mix and enhance existing ones including:
- Network and device authenticationAuthentication is the call centre security process step in which a user's identity is confirmed. We check they are who they claim to be. It requires the use of one or more authentication factors. provides possession-based confidence. Is this call from the customer's registered device? Does the network data match expected patterns? These factors require no customer effort yet add significant securitySecurity is one of three key measures of Call Centre Security process performance. It is usually expressed as the likelihood that the process allows someone who isn't who they claim to be to access the service (False Accept)..
- Behavioural transaction monitoring examines what customers do, not just who they claim to be. Unusual transaction patterns trigger additional scrutiny regardless of authentication outcome.
- Risk-based decisioning orchestrates all factors dynamically. Low-risk requests might proceed with voice alone. High-value transactions require multiple factors. The system adapts to both customer behaviour and threat landscape.
These layers work together, compensating for individual weaknesses. When voice biometrics faces a synthetic speech risk, other factors maintain security.
The Real Threat
Voice cloning for biometric bypass represents the peak of sophistication - but not the primary risk for most organisations.
For Wealth Management and Private Banking
If you are in these sectors then “whaling” type attacks are a genuine concern. Many of your lower risk relationship interactions are likely to depend on voice authenticationAuthentication is the call centre security process step in which a user's identity is confirmed. We check they are who they claim to be. It requires the use of one or more authentication factors. (often without biometrics), and your high-value clients make it worth spending the time and effort on sophisticated voice clones. You should be evaluating detection capabilities and strengthening authentications for these interactions immediately (probably with voice biometricsVoice Biometrics uses the unique properties of a speakers voice to confirm their identity (authentication) or identify them from a group of known speakers (identification).).
For Everyone Else
The bigger threat is synthetic speech enabling social engineering of your customers at scale. Fraudsters use off-the-shelf synthetic voices (cheapfakes not deepfakes) further enabled by the Large Language Models OpenAI sells to make thousands of calls to your customers to trick them into giving up their knowledge based credentials or authorising fraudulent transactions.
Genuinely authorised (whether with biometrics or not), transactions and an exponential increase in the compromise of knowledge based credentials by automated social engineering are what should be keeping practitioners up at night.
Subscribe for New Content
The Irony and the Future
There's irony in warning about biometric authenticationAuthentication is the call centre security process step in which a user's identity is confirmed. We check they are who they claim to be. It requires the use of one or more authentication factors. whilst selling biometric authenticators. But that's beside the point.
Some form of centralised digital or decentralised cryptographic identity, a version of which he proposes, probably is the future. The Nordic countries have great success with schemes like BankID and there are nascent digital id schemes in several countries. But millions of customers need service today, not when perfect (and you can bet they won’t be either) solutions arrive. If you are interested in this field then I’m a big fan of Jamie Smith’s writing on this.
Organisations must work with current technology and existing customer behaviour. If you are using or considering voice biometricsVoice Biometrics uses the unique properties of a speakers voice to confirm their identity (authentication) or identify them from a group of known speakers (identification). then:
- Understand it as just one (albeit pretty good) layer in your securitySecurity is one of three key measures of Call Centre Security process performance. It is usually expressed as the likelihood that the process allows someone who isn't who they claim to be to access the service (False Accept). architecture
- Ensure robust synthetic speech detectionSynthetic Speech Detection is a mechanism used to protect Voice Biometrics systems from presentation attacks using synthetic speech. It relies on detecting characteristics inherent in the text-to-speech (TTS) generation process., regularly updated
- Evaluate complementary authentication factors such as network and device authentication
- Focus on how to orchestrate your capabilities to achieve the right balance of security, efficiencyEfficiency is one of three measures of Call Centre Security process performance. It represents the actual and opportunity cost of the security process, for example the costs of agent time spent on manual authentication or the missed opportunity for self-service. and usabilityUsability is the primary performance dimension of the security process. Get it right and both security and efficiency flow, but usability is all wrapped up in human psychology. It’s a complicated subject deeply linked to behaviour, not just that of customers, but also of call-centre agents. for your unique context
- Remember that denying legitimate customers service is also a failure
Altman's warning reflects genuine risk, but from an idealist's perspective that doesn't account for operational reality. Perfect security that excludes legitimate customers from accessing an organisation’s services is a non starter.
The organisations I work with understand this. They operate in the messy middle between theoretical vulnerability and practical necessity, building defences that actually work for real customers making real calls today.
Voice biometrics remains one of the most effective tools we have - not perfect, but significantly better than the alternatives most organisations still use. The key is implementing it as part of a considered, layered approach that acknowledges both its strengths and limitations.
I help organisations implement authentication solutions that balance security with the reality of serving millions of customers. If you're wrestling with these challenges, let's discuss how to protect your customers in the world that exists, not the one we wish we had.
